Deciding Between POC and Product: Let Risk Drive Architecture, Timelines, and Quality Gates
Deciding Between POC and Product: Let Risk Drive Architecture, Timelines, and Quality Gates
When a Prototype Goes Too Far
A few weeks ago, I was on-site with a client, lining up what everyone expected would be a simple proof of concept. Just a quick demo to see if the idea even made sense. Honestly, we were thinking short-term, not much risk, low stakes.
But it didn’t stay low stakes for long. By the second afternoon, the energy in the room had shifted. Excited chatter, people forwarding screenshots, someone even called in a team lead who hadn’t seen the demo yet. The momentum surprised all of us.
That’s when the ask dropped and the pressure of deciding between POC and product hit: “Can we just tweak this and deploy?” It happens fast. Stakeholders see something working and—without even meaning to—start treating a test like a finished product. I’ll admit, I’ve been caught up in that wave a few times myself.
But there was one problem. It wasn’t built for production. This is the classic prototype vs product gap: it may look slick up front, but that user interface is usually disconnected from any real backend. The guts just aren’t there yet (see Netguru). Pretending otherwise means scaling fragile code, filling gaps with band-aids, and inviting instability. You might get lucky for a sprint or two, but debt piles up and the rebuild cost only grows.
That set up the fork in the road. We could start over and build the real thing with production in mind. Or we could force-fit what was technically just a demo into a living system. That choice—validate fast or build for scale—is exactly where you need to pause and commit before code. That’s the framework I wish someone had spelled out for me earlier.
I still remember a day—must have been last year—when I spent half an hour debugging a “temporary” workaround left in a prototype, only for the power to flicker in the building and our test environments all went down. (Turns out, the “quick” fix relied on a hard-coded port that happened to be used by the janitor’s computer in the basement. You can’t make this stuff up.) In some ways, the product survived, but I can’t say anyone really trusted it again.
Deciding Between POC and Product: Validate or Build for Scale
The real turning point came in a hallway outside the client’s makeshift war room. Hamid—who’s run his share of rollouts—cut through the noise with something that stuck. “Just name the risk out loud. Is it that they might not even want this, or is it that if it breaks, we’re up at 2 a.m.?” That was the mental click. From then on, I started putting the big risk front and center before anything else, letting it decide how we’d work. It sounds basic, but for me, that awareness was new. I’d spent too many projects blurring that very line.
This is the framework I keep coming back to. Let the dominant risk point the way. You can call it The Decision Playbook: Validate or Build for Scale.
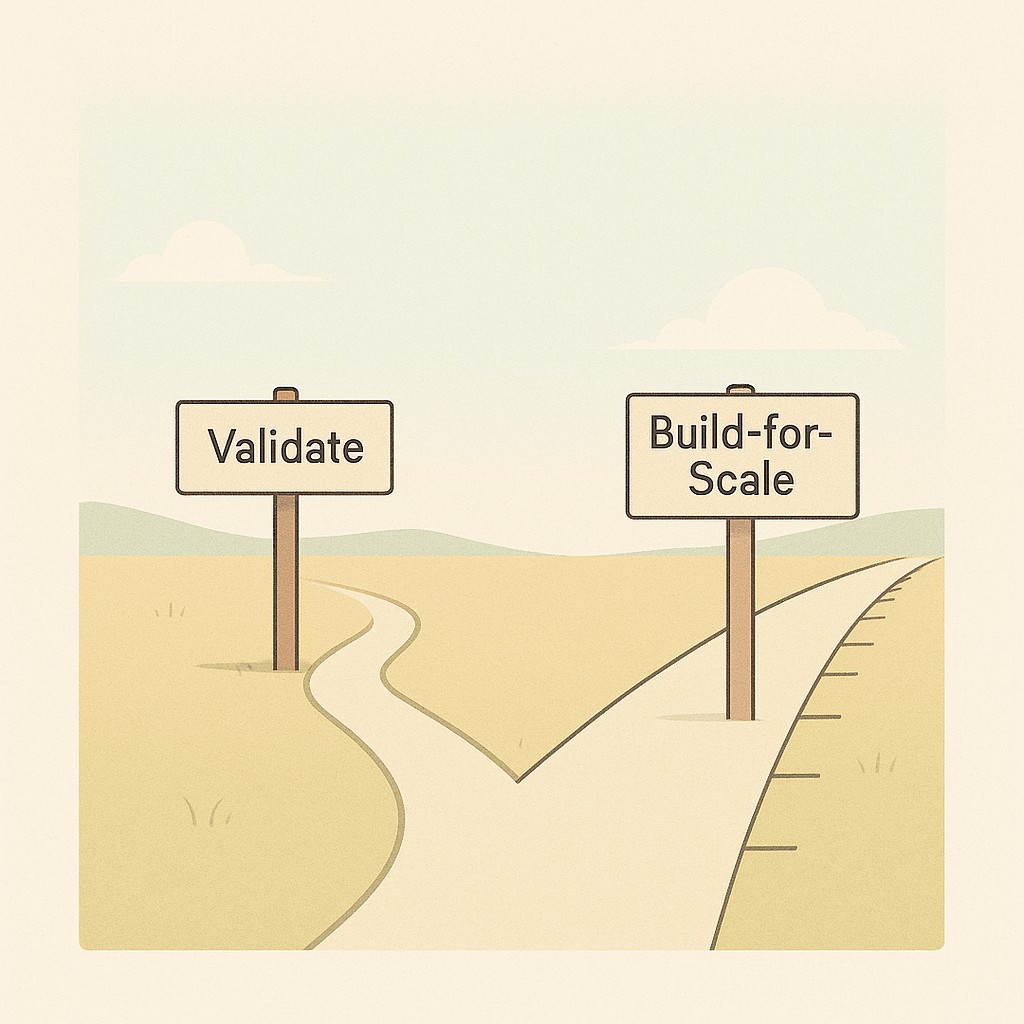
Here it is, drawn sharp: POC vs production are different worlds. It’s there to ask, “Will this really work if we put it into the wild?” That’s what tells you if the idea is worth investing in, versus whether it’s time to start thinking about the real architecture and support.
And I know what you might be thinking. Doesn’t this formal step slow things down, right when everyone’s excited? I’ve wrestled with that, too. But there’s a different kind of pace that matters. The pace where you protect your credibility and your client’s budget. If you blur the lines, you end up spending double—once when you ship a fragile experiment, again when you pay down the debt. Setting the expectation up front and being honest about mode actually keeps momentum healthy. It makes it easier to tell a stakeholder “not yet,” and it shields your team from getting blamed for instability that comes from shortcuts, not incompetence.
Most of my regrets from early projects were from skipping this step and hoping we could clean it up later. Rarely works out.
So declare intent before coding and, before you write a line of code, pause. Write down the riskiest thing: will the client care, or will it scale? Pick Validate or Build-for-Scale. Even printing it on a sticky note helps when pressure hits.
From Framework to Code: Engineering for Your Chosen Risk
If you’re optimizing for Validate, the whole mission is speed and learning. When adoption is uncertain, you want to keep surface area tiny. Strip things down, use the simplest paths, and wire in whatever telemetry or logging lets you watch how users interact. Don’t waste time hardening what might never survive first contact. I always tell teams: delay the polish, instrument the insights. Every shortcut is fair if it gets you answers fast.
On the other hand, Build-for-Scale is a different game entirely. Once reliability, potential rebuild costs, or high-impact failures are on the line, you’ve got to front-load your investment. Modular architecture, robust error handling, and deep observability. This is when service-level objectives (SLOs) and error budgets show up—they give teams objective, user-centered ways to measure and steer service reliability. Suddenly, it’s not just “does it work?” It’s “how will this hold up under real-world load, day after day?”
Honestly, it’s like the difference between trying out a new recipe on a Saturday afternoon versus accepting an order to cater a wedding. When you’re just testing, you can improvise. When the stakes are bigger, you need prep, process, backup plans. The risk shapes the whole approach.
Now, here’s the ugly math I’ve learned the hard way. Shipping a fragile prototype to production isn’t just a technical gamble—it’s a financial one. You might patch things quickly and get applause…until the first instability hits. Outages, bug hunts in weird edge cases, late-night escalations—those rack up internal debt and reputational costs you rarely see until it’s too late. The code gets sticky, rebuilds become exponentially harder, and what seemed “quick” backfires as expensive engineering work.
On the flip side, rebuilding with intention, aligned to the dominant risk, nearly always costs less than cleaning up after public failures. I’ve walked into more than one client call—tired teams, frustrated sponsors—where most of the pain could have been dodged by pausing and saying, “Let’s validate first, then build for scale.” That’s not pessimism; it’s what keeps budgets in check and trust intact.
You see this split clearly in ML POC to production transitions across ML and AI projects. Notebooks and sketchy scripts work in validate mode—throw results up, monitor what matters, move on if it flops. Build-for-scale shifts you to services, endpoints, SLAs. Quick metrics checks and synthetic unit tests are fine when you just want directional insight, but once users touch production, you need real-time monitoring, versioned models, alerting wired in. If you know the mode, choosing tooling and process gets so much simpler.
It’s not about dogma. It’s matching your engineering choices to the risk staring you down. Every time I’ve respected that, projects felt lighter and clients stopped worrying about ugly surprises later.
I’ll be honest, I still fall into the trap now and then. Something about the momentum of a successful demo has a way of short-circuiting my better judgment—especially if folks start forwarding screenshots and the “just one change” requests pile up. I’m not sure I’ll ever be completely immune to it.
Managing Momentum and Setting Boundaries
Then came the question. “Can we deploy this next week?” This is the moment—raw excitement but also the need for discipline. I name the mode up front: “We’re still in Validate. The biggest risk right now is adoption, not reliability.” Labeling the risk isn’t just a technicality. It’s how you frame every conversation from here.
Here’s something that’s easy to miss. Moving fast doesn’t mean pushing experiments into the wild before they’re ready. Real speed, in my experience, is about learning fast or scaling right, depending on which mode you’re in. I used to get swept up by stakeholder buzz and worry that drawing boundaries might look like sandbagging. But the truth is, getting clear about the mode lets you set timelines and technical depth that fit the job—not default to chaos.
Tie every review, test, and sign-off to that declared mode. If we’re in Validate, we run quick functional checks and focus on the data coming back. If we’ve chosen Build-for-Scale, that triggers deeper testing—load, security, resilience. It’s a lot easier to justify quality gates when everyone knows what risk profile we’re working to contain.
This discipline isn’t just process. It shields your credibility and your client’s actual budget. Stay clear on mode, and you’ll avoid scaling throwaway code.
It’s funny—remember that building power flicker I mentioned earlier? That whole mess came back to bite us again later in the project. It became this running joke on the team about our “janitor mode” whenever someone proposed another band-aid fix. We still managed to deliver, mostly because we drew the line (finally) and rebuilt instead of patching that haunted prototype one more time.
From Framework to Action: Locking In Your Decision Early
Before anyone dives into code, get the team in a room—virtual or literal—and make the call clear by deciding between POC and product: Validate or Build-for-Scale. Capture that choice somewhere visible, and put a timestamp on it. This doesn’t have to be ceremonial. Even dropping it into Slack or a shared doc makes sure expectations stick across product, engineering, and whoever’s lurking on the client side right now.
After a few rushed pivots, I started pushing for a one-pager that anyone can scan—no jargon, just practical alignment. At the top, jot down the dominant risk (adoption, reliability, or something else), your chosen mode, and the architecture stance (“bare bones for learning” or “modularized for durability”), including build vs buy decisions. Spell out whether the timeline is “fast fail” (days/week for validate) or “staged release” (weeks/months for scale), and set clear quality gates: is it just sanity checks and data logging, or are you wiring in load tests and security reviews? Add a trigger—what do you need to see to roll back, pivot hard, or start a rebuild? That’s your north star if expectations shift.
When you need clean one-pagers, updates, and stakeholder briefs while you validate or build for scale, use an AI tool to generate clear content fast, keeping communication tight without bogging down engineering time.
Declare the mode, let risk guide everything, and keep your team from accidentally scaling a prototype no one wants to own later. This is the move that shields your time, budget, and reputation—every single time.
Enjoyed this post? For more insights on engineering leadership, mindful productivity, and navigating the modern workday, follow me on LinkedIn to stay inspired and join the conversation.
You can also view and comment on the original post here .
